E20 - Team Finance, FriesDAO, & Layer2DAO Hacked - Profanity Woes Continue - 11/1/2022

╠ Listen idegen.fm ✪ Contact @idegenfm ✪ Show notes wolfdefi.com ╣
Intro
Welcome to I, Degen - A podcast about crypto technology, security, and culture. We balance hype and hate, cutting through the misinformation and ego in search of the signal in the noise.
Listen to I, Degen E#20 directly on idegen.fm, on Spotify, Apple Podcasts, or various other places.
E20 Summary
October is finally over, and we’re going a mile wide and an inch deep on this week’s crypto security news. It would have been a relatively calm week if it weren’t for the ongoing profanity attacks. Let’s dig in.
I, Degen - Weekly Crypto Security Headlines of Interest
DeFi Hacks of the Week
-
- Hack loss was roughly $384,615 USD at the time of the attack, with L2DAO token at ~0.0077. Price has almost fully recovered as of this writing.
Today a hacker was able to gain access to an Layer2DAO multisig on Optimism and drain 49,950,000 L2DAO tokens. They dumped some of the stolen tokens but we were able to negotiate and repurchase the remaining 31,239,677 tokens. - @Layer2DAO
But since the implementation contract only existed on Arbitrum, the fallback method was hit and this meant: the Gnosis Safe contract was successfully created, but not initialized. This slight distinction was what ultimately allowed the attacker to call the function setup owner on the created but not initialized contract and carry out the attack.
-
October 27th, Team Finance Hacked - DeFi Platform Exploited for 14.5M Despite Security Audits
-
October 27th, 2022 - FriesDAO Exploited
FriesDAO is a decentralized social experiment where a crypto community builds and governs a fast food franchise empire via wisdom of the crowd
On October 27th, 5:58PM UTC, friesDAO contracts were exploited by an attacker taking control of our own deployer address through a profanity attack vector. The hacker was able to drain the treasury of its USDC through the refund contract, drain the FRIES tokens in the staking contract, subsequently selling it all into the Uniswap pool. All transactions in the main attack with the refund contract were confirmed in the same block, then three hours later, the attacker came back for the staking pool
-
part 1 - 2,138,705.403949 USDC
-
part 2 - Took all the FRIES out of the pool, then sold for 120.128930112550592565 ETH ($189,954.761991 at the time):
-
-
Looks like @QuickswapDEX @market_xyz @QiDaoProtocol was exploited on polygon again
-
Looks @n00dleSwap has an ERC777-based reentrancy issue and is being attacked, causing a loss of $29K. - @BlockSecTeam
-
Dappnode Liquidity Mining Contract Compromised via Profanity vuln - Confirmed Profanity Vuln
-
The hacker/s ran away with 57.72 ETH and 552.61 GNO (aprox. 165,000 USD)
-
-
October 29th, a attacker exploited Giveth GIVfarm using Profanity vuln - 2
This was not a smart contract exploit. Rather, the keys we used to control the rate of rewards to our GIVfarms were compromised.
The attacker used the compromised keys to change the reward rate for our Mainnet farms to a very large number & then quickly claimed the rewards. -@giveethio
General Crypto Cyber Crime
According to reports, Turkish officials discovered an illegal betting business that used bitcoins to launder criminal profits.
Following the investigation, police enforcement detained 46 people engaged in the fraud and seized $40 million in digital assets.
According to the allegations, the company conducted an illicit sports betting scam and transferred the proceeds to multiple bitcoin accounts.
-
Oct 25th, ZachXBT calls out Monkey Drainer for scamming/phishing ~700ETH in 24hrs
-
October 20rd - FTX API keys connected to 3Commas confirmed to have been exploited
Hack Updates
-
Moola Market Restore Solvency, Resume Deposit And Repayment Functions
-
October Major Incidents from Certik
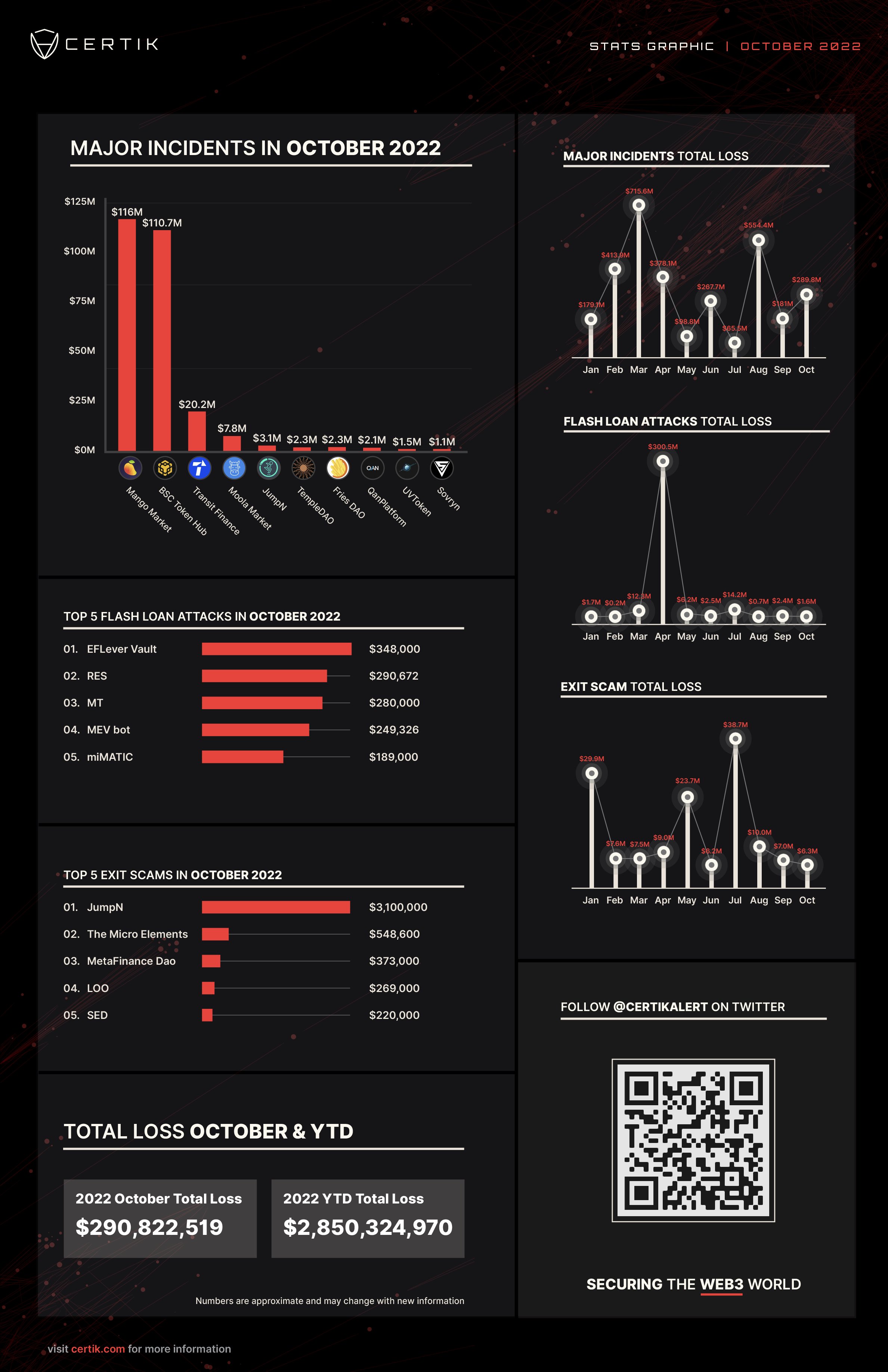 - Certik Twitter
- Certik Twitter
I, Degen Links of Interest
-
Blockchain Dark Forest Selfguard Handbook - Dark Handbook Github
-
Inside the elaborate set-up of a scam HQ, staffed by people forced to scam
-
The SIM Swapping Bible: What To Do When SIM-Swapping Happens To You
-
🛠️ Supermacy Inc launches a visual blockchain transaction explorer “Cruise”
-
Coinbase: BSC Token Hub Compromise investigation and analysis
-
We explore empirical evidence on the risk associated with DeFi protocols, that is, the risk of cyberattacks in the form of hacking incidents, rug pulls or economic attacks as a function of the TVLs of the protocols. - @andresrieznik @ Bittrap.com
We estimate that when a DeFi increases its TVL by a factor of 10, its probability of being hacked increases by 10% or 13%, depending on the data considered for the analysis.
Outro
We do our best to report accurately on the topics we discuss, but we’re not always going to get everything right. Please contact us @idegenfm, @WolfDeFi, @Hunthk11 with corrections or comments!