E19 - Alpha Hunting w/Threat Intel Bots & Devcon 6 Security Talks Gem Hunt PT1

╠ Listen idegen.fm ✪ Contact @idegenfm ✪ Show notes wolfdefi.com ╣
Intro
Welcome to I, Degen - A podcast about crypto technology, security, and culture. With a healthy balance of enthusiasm and skepticism, we dig into a weekly look at crypto, cutting through the misinformation and hype in search of signal in the noise.
Listen to I, Degen E#19 directly on idegen.fm, on Spotify, Apple Podcasts, or various other places.
E19 Summary
Finally, a break in the storm as things calmed down in the third week of a brutal October. This week, we will discuss the Moola Markets price manipulation and the Cosmos vulnerability. We’ll dive deep into a few choice DEVCON 6 security talks and follow the rabbit hole from one of the talks into decentralized threat intel bots.

Upcoming Events of Interest
-
Forta Bot Competition - Attacked Protocol/Asset Source Identification Bot. October 11th-November 1st. They will only take the first ten submissions.
-
ETH Lisbon Hackathon, 28-30 Oct
-
Rekt is doing a ‘secret’ meetup in Lisbon as well
I, Degen - Weekly Crypto, Security, & Other News Headlines of Interest
Using initial funding of 243k CELO (~$180k), the attacker supplied 60k CELO in order to borrow 1.8M of the protocol’s native token, MOO, which could itself be used as collateral to borrow against other assets.
Then, using the remaining CELO to buy MOO on Ubeswap, the attacker pumped the price of their MOO collateral allowing them to borrow the remaining assets on the protocol, draining all liquidity
-
October 15th, One of the Mango Markets manipulators came out and became a meme for ‘deploying a highly profitable trading strategy’. Later (October 18th), he proposed a solution to make lending protocols more robust (less susceptible to price manipulation attacks). The Tweet ignites a question again of if this was a hack or not.
A chain is safe from the critical vulnerability as soon as ⅓ of its voting power has applied the patch. Chains should still seek to patch to ⅔ as quickly as possible once the official patch is released.
No reports of exploitation in the wild.
The article also notes that fewer hacks have taken place on Cosmos. I wonder why that is?
Also, issue this different issue for Cosmos:
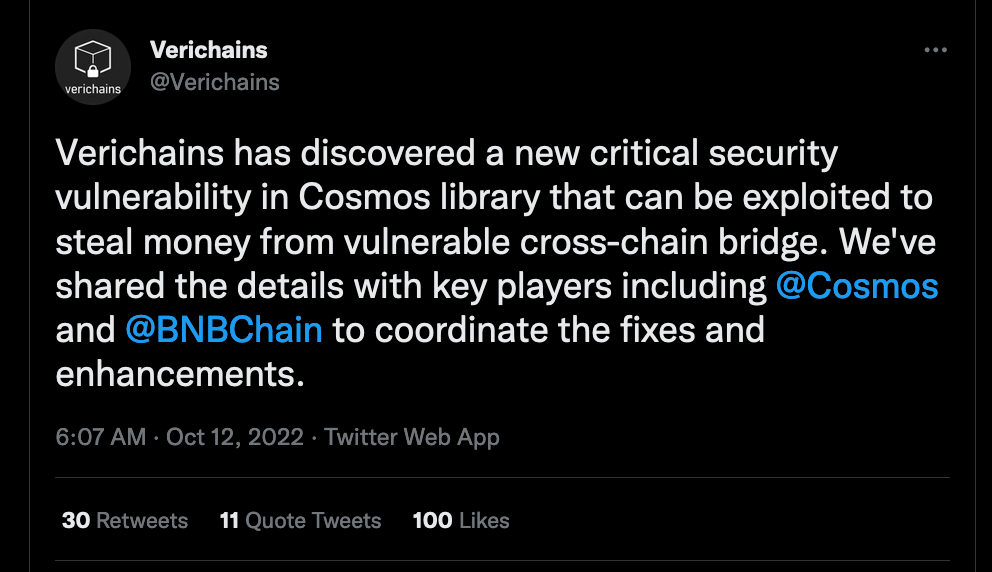
And Cosmos-SDK Security Advisory Dragonfruit from October 8th
Recently, the core Cosmos team became aware of a high-severity security vulnerability that impacts all users of the IAVL merkle proof verification (“RangeProof”) system, for all versions of the IAVL software.
Nice work to all involved to uncover and path these before exploit.
RayNetwork, a DeFi ecosystem for Cardano was attacked.
On October 3 and October 10, 2022 an attacker attacked RayStake by spoofing a stake key in the payment address, causing the vending machine to send rewards of a specific stake key to the attacker’s address.
the attacker accessed a total of 5,554,113 XRAYs and 112 XDIAMONDs. He sold these funds through Minswap DEX and Sundaeswap for 412,253 ADA.
worth ~139,540.95 USD at time of this writing.
- DeFi protocol Olympus DAO lost almost $300,000 in OHM tokens in a security exploit today.
- The attacker later returned all of the funds following a negotiated deal.
This was a new Bond Protocol contract that was still in testing. So, there were limited funds in the pool.
The hacker has returned all of the stolen tokens. The team successfully tracked the perpetrator, after which the hacker agreed to return the funds, a spokesperson from Olympus DAO told The Block.
According to court documents, Meiggs and Harrington targeted executives of cryptocurrency companies and others who likely had significant amounts of cryptocurrency and those who had high value or “OG” (slang for Original Gangster) social media account names.
E19 Devcon 6 - Security Talk Gem Hunt
1. Rug Life: Using Blockchain Analytics to Detect Illicit Activity and Protect Yourself
Presenter: Heidi Wilder - Special Investigations at Coinbase
Talk Abstract
Learn how to use blockchain analytics to identify and protect yourself from the latest rugs, hacks, and scams. The purpose of this talk is to discuss: - How to (automatically) identify illicit activity on the blockchain - Typologies of the latest rugs, hacks, and scams - Tracing where funds from a latest rug/hack/scam have gone - How to protect yourself as a dev
Talk Notes & Highlights
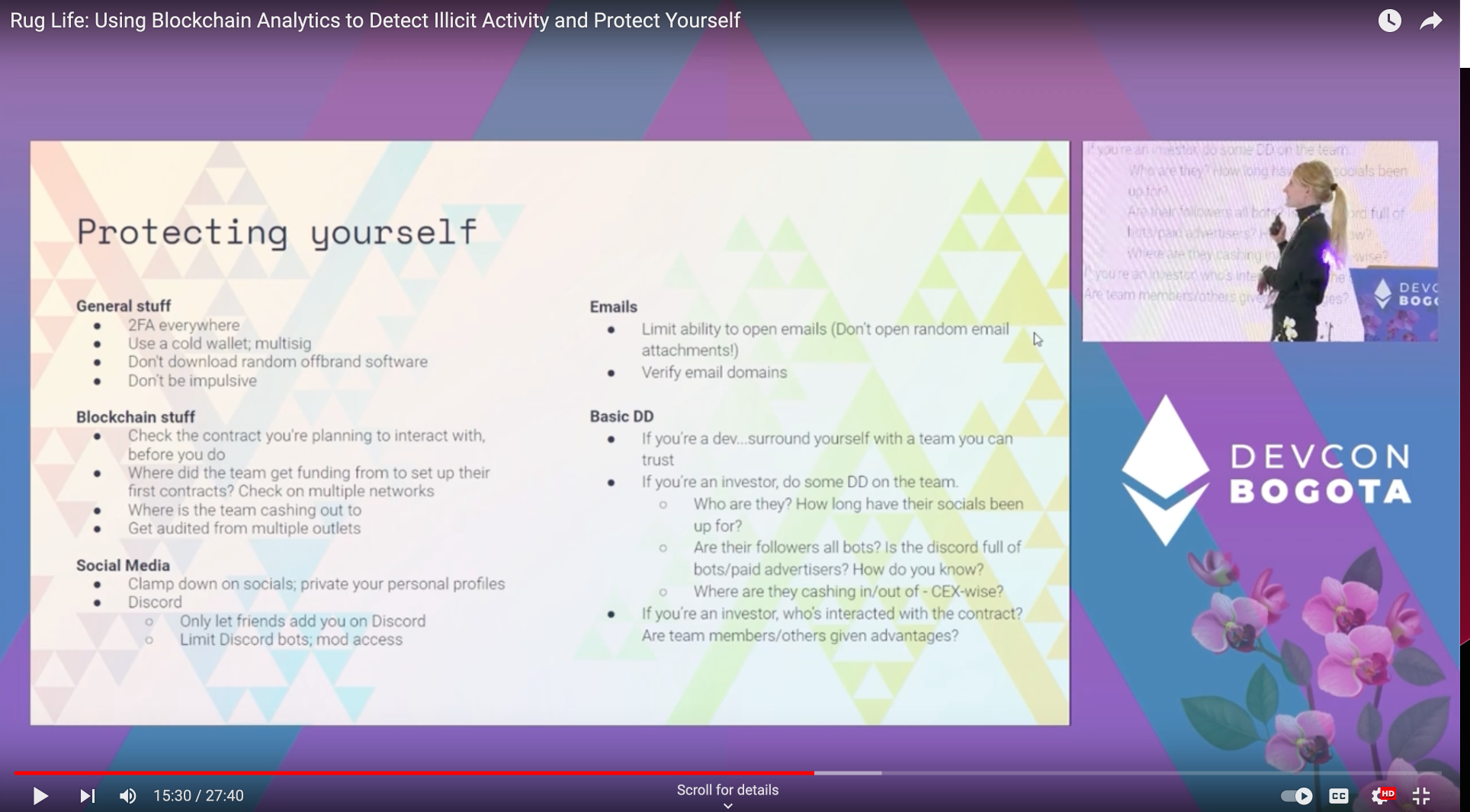
Detection Methods - - alerts to monitor for large flows of funds
Detecting weird stuff in advance
- devs: Monitor what is going on with your contracts.
Nomad could have see wierd stuff going back to July and probably prevented
-
use caution with twitter investigators. During Mango Markets price manipulation, she saw various addresses being thrown out that weren’t involved in the hack
-
cool look at the tracing of the Ronin funds.
-
Social Engineering attacks are a common thread as the initial attack vector. Particular nation-states are known to use it often.
-
Privacy Protocols are relatively easy to track enormous volume hackers because they move so much at once
2. Crosschain Security Considerations for the Degen in All of Us
Presenter: Layne Haber
Talk Abstract:
Crosschain applications (xApps) are often considered too risky, but this viewpoint is divorced from reality. People will use these applications and it is our responsibility to understand the security implications. xApp developers must be able to reason about concurrency and asynchrony across two different networks, as well as understand the trust assumptions introduced by the data transport layer. By understanding this, we can allow users to engage in risky behavior in the safest way.
- Contagion Risk
Generally, in economics, a contagion is the spread of an economic crisis from one financial institution, market, or region to another.
Taxonomy of bridges
- native verified - complicated
- externally verified
- optimistically verified
Bridges are hard.
Validation of consensus and state transition is coming soon and will likely be the gold standard but not ready for prime time yet.
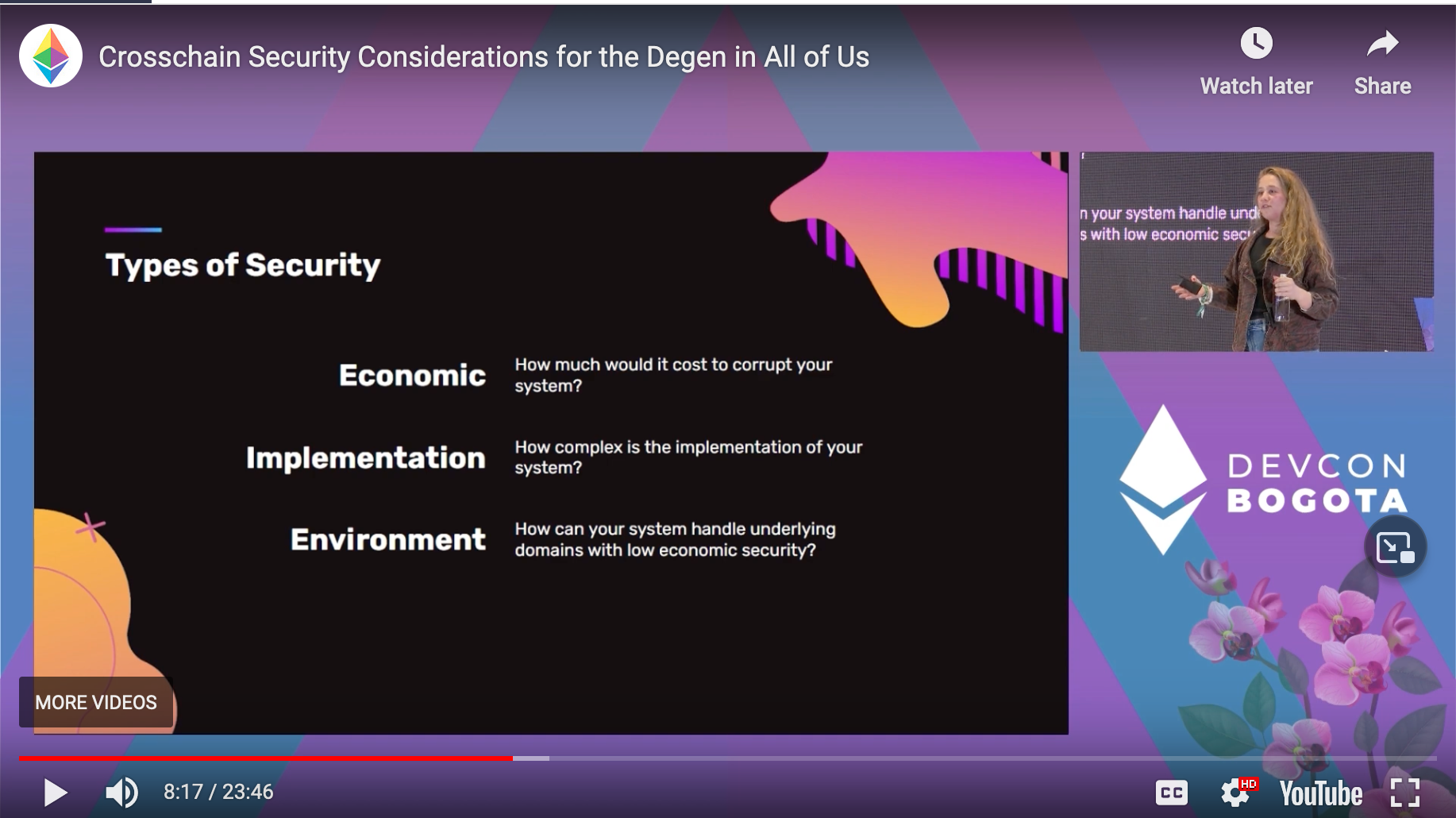
Type of security
-
Economic - How much would it cost to corrupt your system?
-
Implementation - How complex is the implementation of your system? Also, your dev environment. Audits, fuzzing, bug bounties, etc.
-
Environment - How can your system handle underlying domains with low economic security?
Winner: Environment Security 1. Optimistic 2. External 3. Native
Most bridge hacks we see now are Implementation based.
Q: Why do we see so many hacks?
A: New teams, resource-constrained, and shortcuts are taken.
What can users do?
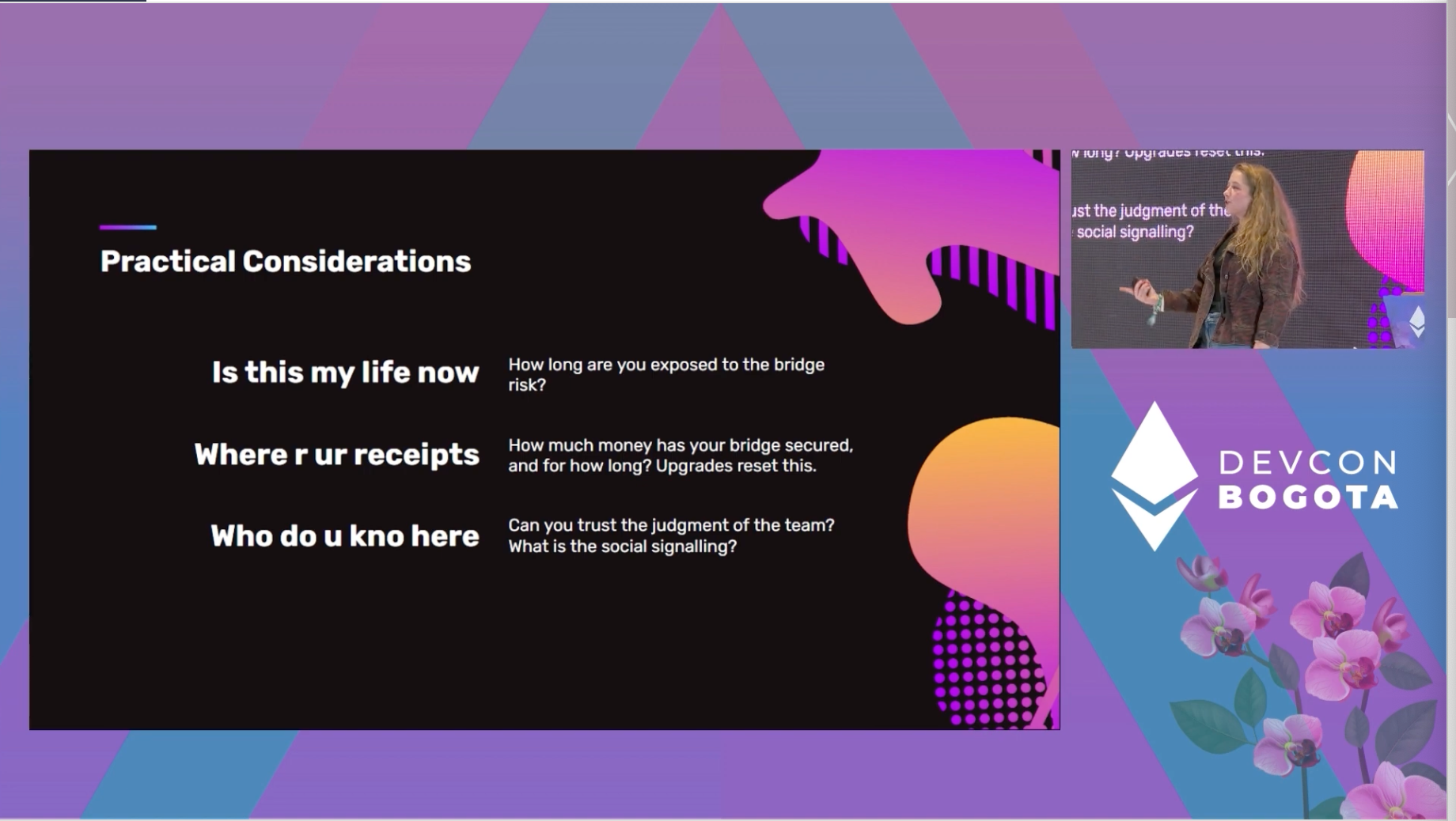
Lindy Effect resets on upgrade.
Lindy Effect is a theorized phenomenon by which the future life expectancy of some non-perishable things, like a technology or an idea, is proportional to their current age.
3. Decentralized Threat Detection Bots
Presenter: Jonathan Alexander CTO @ Open Zepplein & Co-founder @Fortanetwork
Talk abstract:
Decentralized threat detection bots are a recent area of research and development for protecting the ecosystem. This talk will cover concepts and recent research on detection bots and implementation patterns including heuristic-based, time-series based, multi-block, and TX simulation. Examples involving prior exploits will be included, as well as tools, limitations, the potential for automated threat prevention, and areas for further research.
Talk notes & highlights:
Multiple leading security audit firms are beginning to make recommendations on post-deployment smart contract monitring.
- Protocol assumption invariants
- state of critical protocol variables
- known protocol risks that have been considered acceptable
- privileged protocol functionality and transfer of privilege
- on-chain / off-chain /cross-chain synchronization (oracles, bridges)
- external contracts that the protocol relies on or is exposed to
- identified user and protocol attack patterns
Smart Contract Attack Stages
1. Funding - new account, mixer, CEX, bridge transfer
2. Preparation - contract deployment
3. Exploitation - flash loans, transfers, flashbots, re-entrancy, etc - more than 1/2 attacks are non-atomic (more than one tx)
4. Laundering -
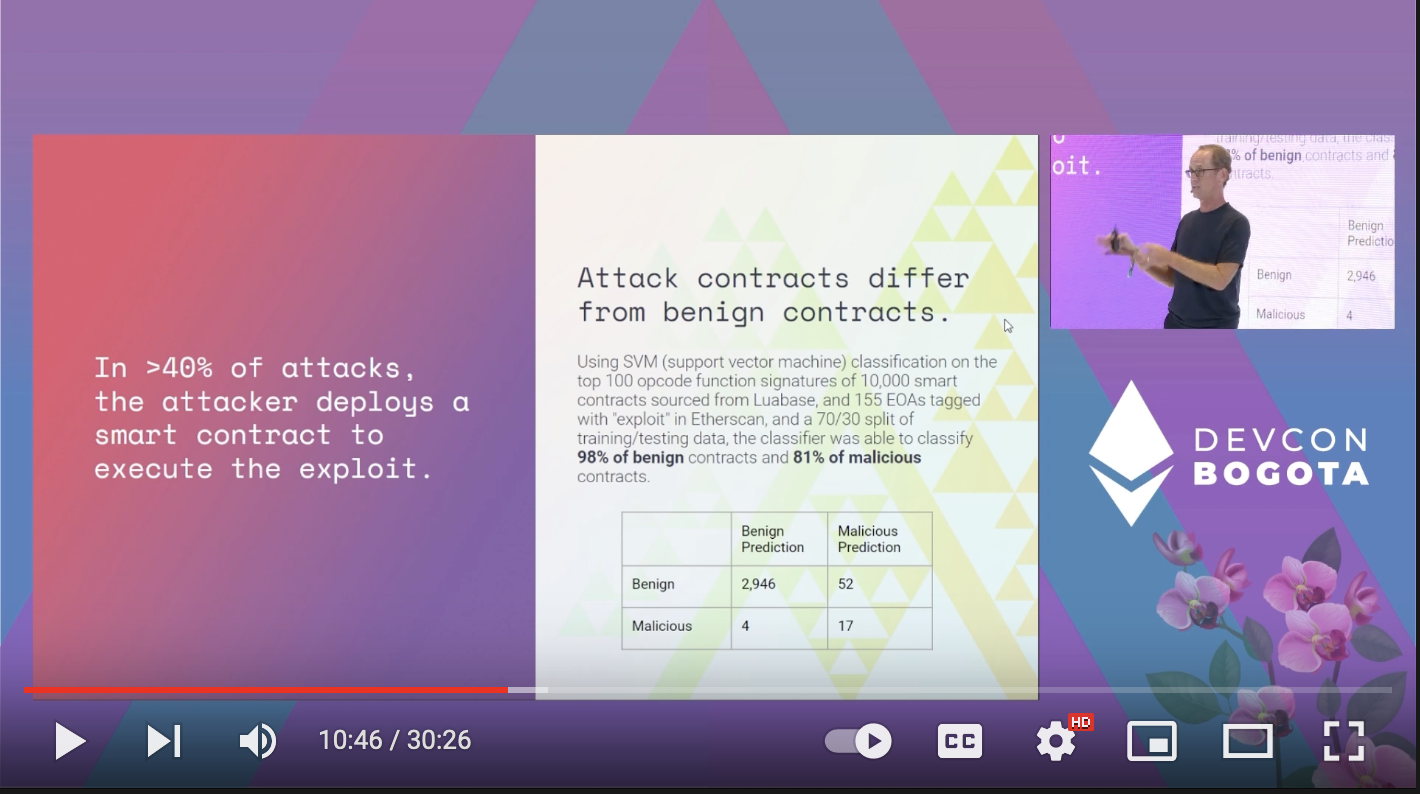
Similar results with bytecode analysis
Fraud-based attacks like Ice Phishing can predict with 95% precision with heuristics!
Forta is a real-time detection network for security & operational monitoring of blockchain activity
Lots of great bot examples, including ML models to do things like: - Smart Price Change Detector - Time Series Analyzer - Contract Destructor
Challenges: - Atomic Attacks - private txs - monitoring secrecy - response latency
Future Areas of research: - private scan pools - mempool Tx Scanning - on-chain alerts
This opens the question up:
Can we find Threat Intel Alpha? Let’s see…
https://explorer.forta.network/
Other Cool Devcon 6 Talks we reviewed
-
Battle of the Bridges: Untangling the Tradeoffs of Various Bridge Designs
-
How to Not Be Worth Kidnapping - Ryan Lackey
-
The $10B Problem - web3 Security Against Coordinated Adversaries Julia Hardy & Adam Hart from Chainalysis
Bored Ape Yacht Club Discord hacked, Ronin Bridge compromised, the news articles are fraught with Ethereum exploits. Chainalysis has identified that these attacks are often executed by a small circle of well-funded, well-coordinated adversaries. In this session, Chainalysis examines how these actors operate, how we investigate the flow of funds to try to disrupt attacks, and how the web3 community can work together to raise costs for attackers using the transparency of public blockchains.
Tether Approval Scam - 83MM in a year! more than 20k victims have been tracked in connection with scam.
I, Degen E19 - Links of Interest
-
Uniswap V3 Development Book - Great free book that will guide you though the development of a decentralized application. Book was funded though a Uniswap grant.
-
I added this to last week’s notes too, but I wanted to mention it on the show as well. Reminder to revoke old contracts that have approval on your addys at revoke.cash
-
Interesting allegation of crypto bots being caught gaming twitter polls on Reddit
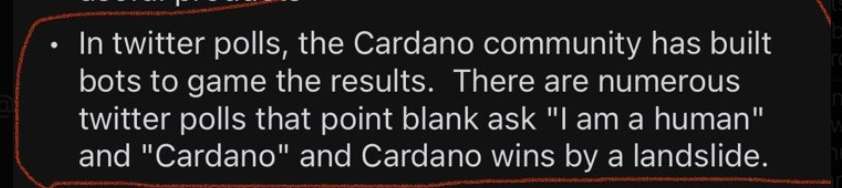
It would be interesting to see if we can find proof of this.
-
Mudit Gupta, CISO at Polygon weighs in on Bogota safety concerns
-
Hans Niemann files defamation suit against Carlson, Nakimura, & Chess.com
I, Degen E19, Maybe list
-
Oddly, the term honeypot has a different meaning in crypto security lexicon. It seems to describe anything that is a target for attackers, not a target that has been expressly set up to draw in attackers.
-
Tech lead at Arbitrium drops trivial vuln in BitBTC bridge (to Optimism)
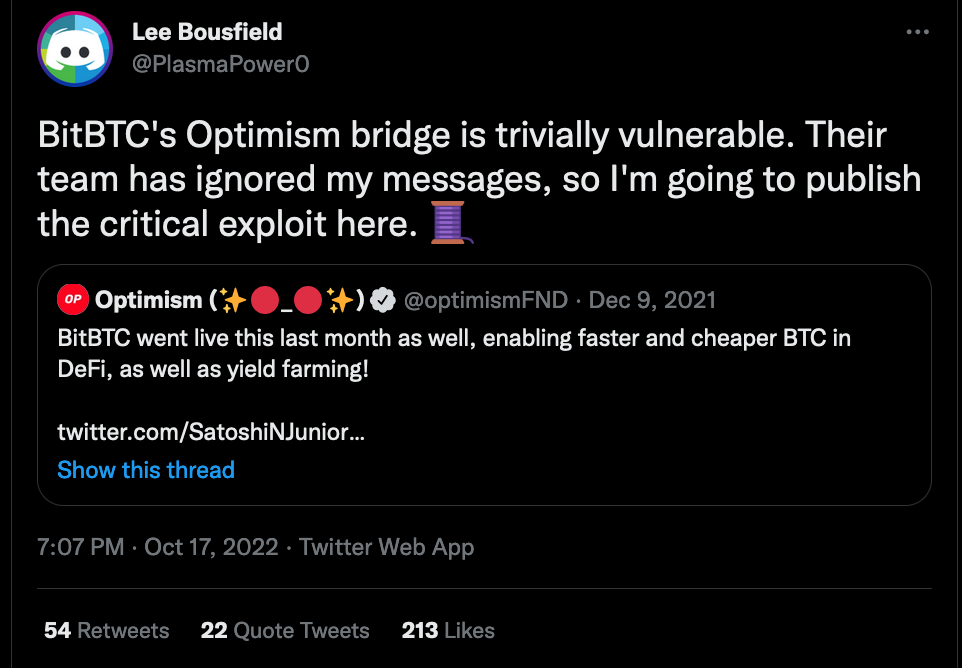
- Questions about responsible disclosure
- If any funds were actually at risk
- Maybe clout farming?
Outro
We do our best to report accurately on the topics we discuss, but we’re not always going to get everything right. Please contact us @idegenfm, @WolfDeFi, @Hunthk11 with corrections or comments!